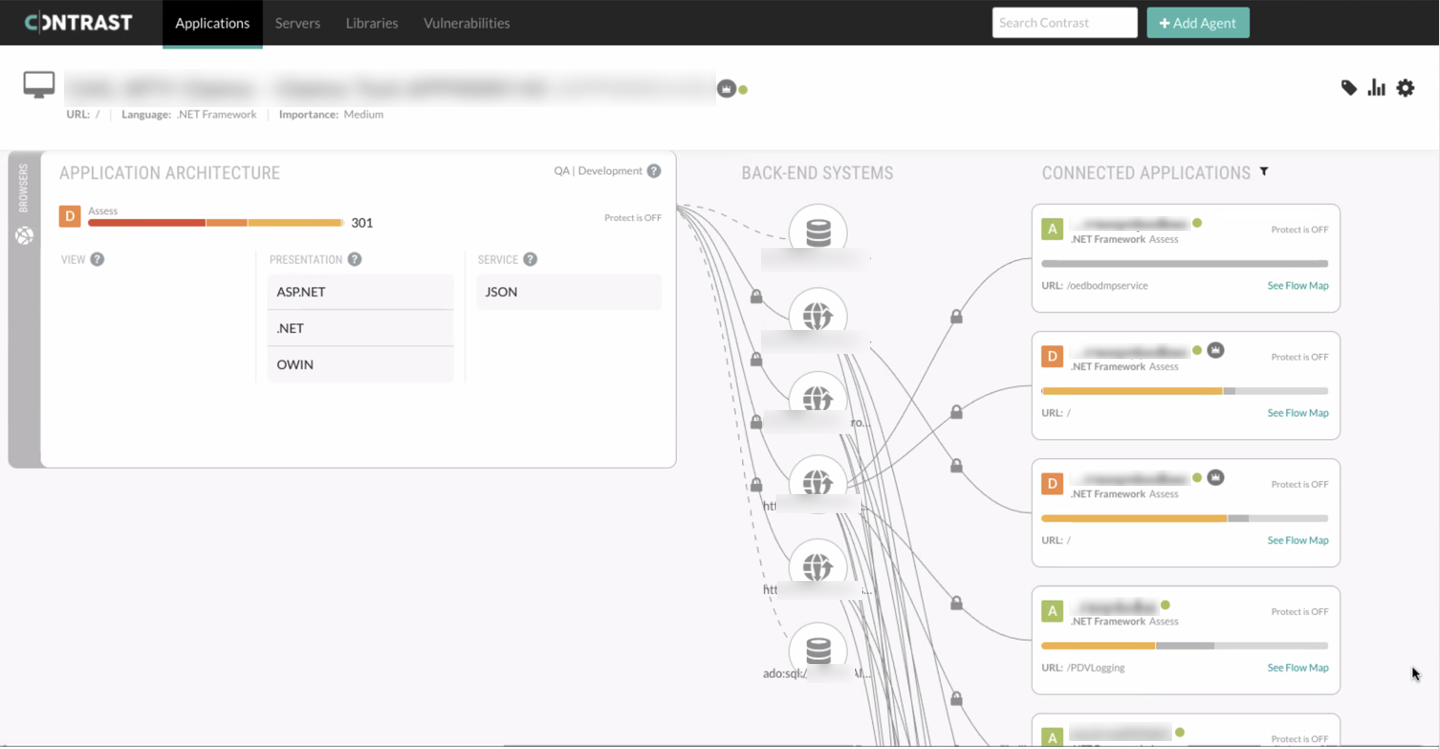
Threat Modeling
Contrast Assess monitors an application's incoming and outgoing connections, as well as what assets the application uses. This application diagram can be utilized to speed up threat modeling by providing automated answers to many questions that would otherwise be asked of the development team.
Flow Map - Quick Threat Model#
In addition to finding security vulnerabilities inside application, Contrast uses its security telemetry to map out the application and its connections. This flow map highlights major parts of the technology stack and shows if/how differend security-monitored applications connect. This diagram can be used in threat modeling discussions with development teams to save time on architectural questions.